Top 20 VPNs for Nintendo
There are many reasons you should utilize a VPN with your Nintendo Switch. One of many can be that you're hoping to sidestep geographic...
Top 20 VPNs for Chromecast
Chromecast is Google's form of a Roku or USB dongle transforms your ordinary TV into a SmartTV, and permits you to get to streaming...
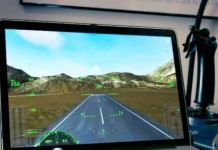
Top 10 laptops for flight simulator in the US 2023
You may have spent a lot of time playing different games, but the excitement of Flight Simulator is unrivalled. When you seat on the...
Top 10 laptops with 144hz screen in the US 2023
The type of GPU and its ability to attain particular FPS levels for certain games influence the screen selection. When it comes to laptop...
Top 20 VPNs for Chromebook
Searching for a VPN for your Chromebook? Before you make a plunge, you ought to realize that some VPNs don't chip away at Chromebooks....
Why Have Scraper APIs Become So Popular?
Web scraping APIs existed as long as the web itself. However, the usage and functionality of scraping have shifted dramatically in the past few...
Top 10 best laptops for Serato DJ in the US 2023
Every DJ has that one time in their lives when they decide to pursue a career as a DJ. To get started as a...
Top VR Sports Games to play on your PC
Most people would think VR is the perfect medium for sports games. Unfortunately, this is far from reality. While VR adds immersion through physical...
Playstation confirms 5 high Severity(8.9) vulnerabilities on PS4/PS5
Microsoft's PlayStation has 5 vulnerabilities that can be exploited by hackers or techies that love to hack.
The following vulnerabilities are exposed for educational...
How to recover data from Office 365? Best data protection standards discussed.
You've made the switch to Office 365 to reap the benefits of the cloud.
It is just as important to ensure that your data is...