Make your dream come true with Startup India’s new initiative “Together 2022”
In today's changing times, everyone wants to open their startup, however, just thinking is not enough because the biggest challenge one has to face when trying to open any startup is...
Analysts Claim That Arresting Canadian Ransomware Attacker is a Major Step
An Ottawa man was arrested this week after approximately two probes by Canadian and US law enforcement officials. He is suspected of committing several ransomware cyberattacks on businesses, administrations, and citizens.
The...
A new phishing campaign on Twitter is attacking verified accounts
Twitter verified profiles are now being attacked as part of a massive phishing attempt that exploits Twitter's decision to remove the verified badge from numerous verified accounts. The initiative distributes an...
More than 300,000 MikroTik devices have been identified to be susceptible to remote hacking...
Due to a security flaw, MikroTik routers were discovered to be potentially vulnerable. The weakness has the potential to be exploited, resulting in DDoS attacks and malware penetration. There are 300,000...
Fitness Industry Facts and Statistics
Because individuals are becoming more health-conscious in today's world, the fitness sector is on the rise and will continue to develop dramatically over time. The gyms and yoga centers are becoming...
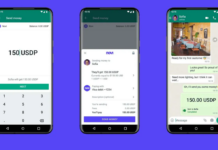
In the United States, WhatsApp is launching a test program for bitcoin payments
WhatsApp has introduced a new trial program that allows a "limited number" of individuals in the United States to send and receive money using cryptocurrencies from within a chat. Payments are...
For Facebook and Instagram in India, Meta has announced new regulations for social issue...
For marketers in India, Meta is releasing new regulations for advertisements on social topics on Facebook and Instagram. Anyone airing commercials on social concerns will need to be authorized under the...
APT15 aka Nickel hacked many nations including America and Europe
According to a report on Microsoft's blog, the Microsoft Digital Crimes Unit (DCU) has confiscated 42 websites used by the China-based hacking gang Nickel to attack companies in the United States...
Apple vs Epic Games and guess who is winning?
Apple's request to postpone a Dec. 9 deadline to comply with the judge's directive, which would allow app developers to lead customers to payment methods outside the company's store, was approved...
How did Amazon and various other companies were breached?
The issues affect Amazon WorkSpaces and other cloud services that employ USB over Ethernet, and might allow attackers to disable security and get kernel-level privileges.
Researchers discovered a number of high-security flaws...