Last Updated on 16/12/2021 by Riya
Researchers have presented a new exploitation method in which the Bluetooth element of a device may remotely collect network credentials and manipulate traffic on a Wi-Fi chip. The new threats target “combo chips,” which are specialized chips that can deal with a variety of electromagnetic wave-based wireless networks, including Wi-Fi, Bluetooth, and LTE.
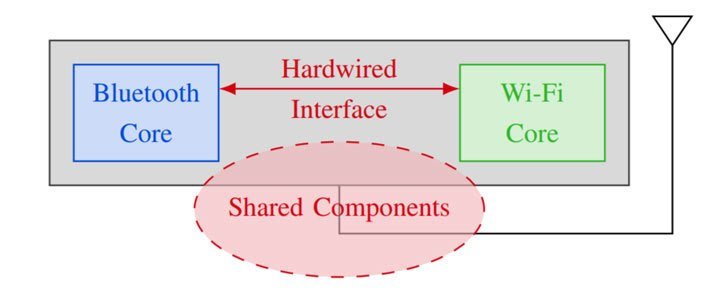
Rather than connecting straight to the mobile operating system, wireless chips can broaden capabilities to other wireless chips by employing the similar method that they apply to mediate access to the resources they offer, such as the transmitting antenna and wireless medium.
Coherence relates to a system in which Bluetooth, Wi-Fi, and LTE utilize the equivalent parts and resources – such as antennae or wireless spectrum – and must prevent collisions when running on the same wavelength to synchronize spectrum usage.
This approach is being adopted by chipmakers to enable Wi-Fi and Bluetooth to run in parallel. While these combined wireless chips are necessary for high spectrum access, coexistence interfaces also present a side-channel vulnerability, as proven by the team of experts at the Black Hat security event held last year.
The threat class termed “Spectra,” is premised on the reality that transmissions happened in the same spectrum and that wireless chips are necessary to arbitrate channel access. This removes the barrier between Wi-Fi and Bluetooth, allowing spectrum access, data exposure, and potentially lateral privilege elevation from the Bluetooth chip to the Wi-Fi chip for code execution.
Furthermore, the experts discovered that an attacker with access over the Wi-Fi core may examine Bluetooth traffic, allowing hackers to know the keystroke timing on the Bluetooth keyboard and, as a result, they exploit it. The potential to re-create the submitted text is granted by this keyboard.
Users should eliminate unwanted Bluetooth pairings, abandoned Wi-Fi networks, and limit the usage of cellular rather than Wi-Fi in crowded places to lower the threat of such wireless cyberattacks.










