Last Updated on 08/12/2021 by Riya
The Moobot botnet is exploiting a known remote code execution (RCE) flaw in Hikvision products (CVE-2021-36260) to deploy a Moobot that performs distributed denial of service strikes, according to research published by FortiGuard Labs.
Hikvision, headquartered in China, claims to be the “world’s largest video-surveillance devices distributor”.
When an adversary uncovers a susceptible system, a downloader distributes the malware, that FortiGuard recognized as Moobot, a Mirai version containing Satori code traces. Sartori is yet a further Mirai-based botnet, one of the thousands sprung out of the primary source malware.
In studying the binary, the researchers learned that it contained the data string “w5q6he3dbrsgmclkiu4to18npavj702f,” which is employed in the “rand alphastr” method.
“It is employed to create numbers and letters for a variety of benefits, including naming a setup procedure and collecting data.”
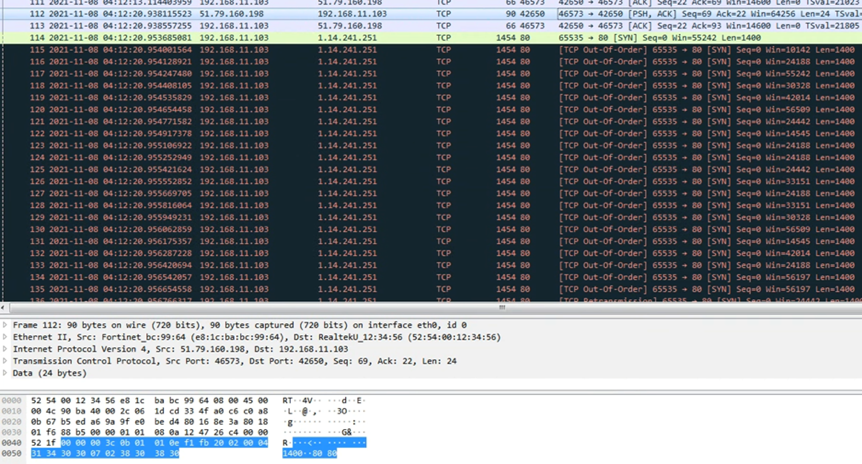
The DDoS attack is initiated when it forms a link with the command-and-control server (C2), according to the study, which appears like the above.