Last Updated on 27/01/2022 by Nidhi Khandelwal
Since the beginning of December, researchers from Bitdefender’s Mobile Threats team have intercepted over 100,000 malicious SMS messages attempting to spread the Flu Bot malware.
The new round of attacks is believed to have been particularly active in Australia, Germany, Poland, Spain, Austria, and Italy, among other nations, beginning in mid-January and moving to fresh countries such as Romania, the Netherlands, and Thailand.
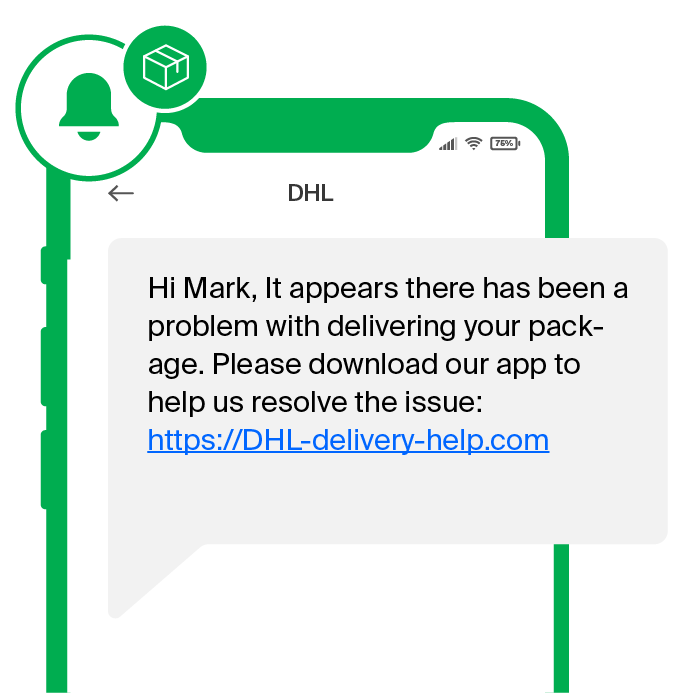
Smishing is the primary delivery mechanism used by FluBot (aka Cabassous) campaigns to target potential victims, in which users are deceived into clicking a link that installs the malware after receiving an SMS message with the inquiry “Is this you in this video?”
FluBot isn’t the only one. Between December 6, 2021, and January 17, 2022, another Android trojan known as TeaBot (aka Anatsa) was discovered on the Google Play Store in the form of an app called “QR Code Reader – Scanner App,” which received over 100,000 downloads while distributing 17 different variations of the virus.
BitDefender discovered four other dropper apps — 2FA Authenticator, QR Scanner APK, QR Code Scan, and Smart Cleaner — that had been available on the Play Store since at least April 2021 and transmitted the TeaBot virus.
Another interesting tactic used by the operators is versioning, which involves sending a benign version of an app to the app store in order to avoid Google’s review process, only to later change the codebase with extra malicious functionality through updates.
The billing fraud, also known as “fleecewear,” is reported to have affected 105 million people in over 70 countries, with the majority of victims in Egypt, Finland, India, Pakistan, and Sweden.










