Last Updated on 24/11/2021 by Riya
A new cybercriminal group misused ProxyShell and ProxyLogon vulnerability to enter into Microsoft Exchange servers. A group of Researchers from TrendMicro firm has discovered the cyber attack. According to the researchers ‘TR’, a hacking group is responsible for cyber attacks.
In the past, this group has distributed numerous emails laden with malicious attachments such as IcedID, Qbot, Cobalt Strike, and SquirrelWaffle. They usually leverage stolen internal reply-chain emails to avoid being detected by cyber security firms.
How this group take advantage of Exchange servers?
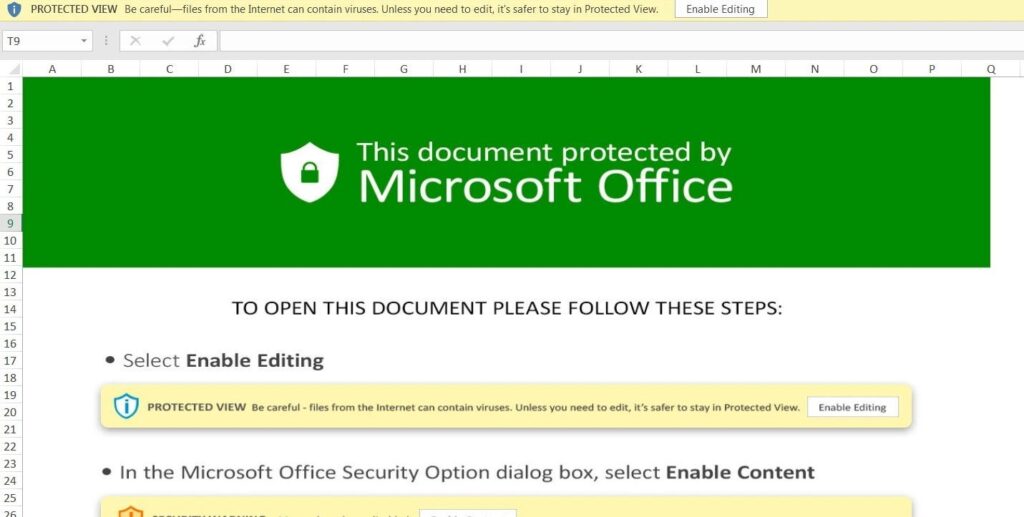
After getting access to the exchange server the group of hackers sent the malicious attachments to the people via email and request them to tap on the attachment. Once the user hits the link they will be redirected to the page where the recipient will be asked to Enable Content option to access a protected file.
The group curates these emails in such a way that the recipient begins to believe they are genuine. The risk of such cyber attacks arose when suddenly cybercriminals started attacking major companies across the world, after investing the matter briefly the security researchers discovered two vulnerabilities named ProxyLogon and ProxyShell which helps a hacker to circumvent authentication and try to imitate the administrator.
However, later Microsoft had patched ProxyLogon and ProxyShell, unfortunately still few servers are left unpatched which are probably at risk of being compromised.










