Last Updated on 22/11/2021 by Sunaina
On Monday, Kaspersky sent two advisory to consumers, warning them of a vulnerability that can result in unbootable devices and a phishing effort involving messages sent from a Kaspersky email address.
The vulnerability, disclosed to Trend Micro via its Zero Day Initiative (ZDI) by researcher Abdelhamid Naceri, affects Windows versions of Kaspersky Anti-Virus, Internet Security, Total Security, Small Office Security, Security Cloud, and Endpoint Security products.
The vulnerability, identified as CVE-2021-35053, is connected to Firefox and may be used to launch denial-of-service (DoS) attacks.
“Possible system loss of service if Firefox browser settings are changed arbitrarily.” “An attacker might modify certain Firefox browser settings files and then reboot the system to render the machine unbootable,” Kaspersky warned in an alert.
Patches for each of the affected items have been issued by the firm. ZDI has yet to issue an advisory outlining this vulnerability, although it’s worth mentioning that the company is working on three advisories for vulnerabilities uncovered in Kaspersky products by Naceri in August.
On Monday, Kaspersky warned that a recent spear-phishing attempt targeting Office 365 credentials included emails purportedly issued by the firm. The phishing emails alert recipients of a new fax and are intended to get users to visit websites set up to steal Microsoft credentials.
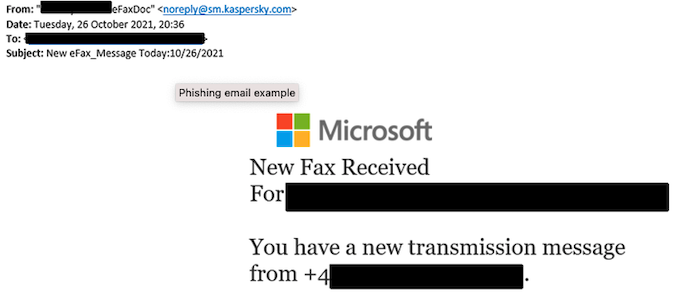
“These phishing attempts rely on a phishing kit we call ‘Iamtheboss,’ which is used in tandem with another phishing kit called ‘MIRCBOOT,'” Kaspersky added. “The action might be linked to many cybercriminals.”
Some of these emails are sent from “noreply(at)sm.kaspersky.com.” The emails were sent using Amazon’s Simple Email Service (SES) and a valid SES token supplied to a third party during the testing of Kaspersky’s 2050.earth website, which is hosted by Amazon. The site is “about the future as viewed by futurologists, scientists, and Internet users from all around the world.”
“When these phishing assaults were discovered, the SES token was promptly cancelled.” “At 2050.earth and linked services, no server penetration, illegal database access, or other malicious activity was discovered,” Kaspersky claimed.










