Last Updated on 05/12/2023 by Dolly
Cybersecurity Threat Analysis
Bitdefender experts have just revealed that they believe the notorious Hive Ransomware is making a comeback as Hunters International. The cyber threat landscape looks to evolve with a successor, despite the attempts of the FBI and Europol to dismantle it in January 2023.

Coding Strategies and Intersections
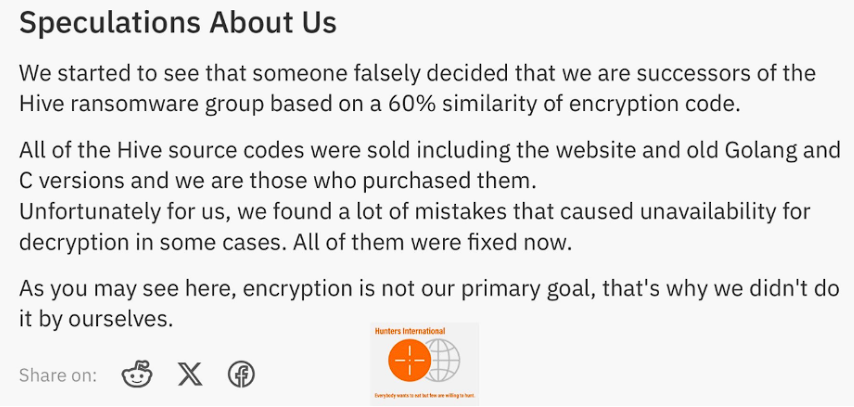
According to the blog post published by Bitdefender, the leadership of Hive has made strategic actions, including suspending operations and transferring assets to the newly recognized threat, Hunters International. Security analysts have found worrying similarities in the codes of the two groups, suggesting a 60% code match.

The Financial and Administrative Freedom of Hunters International
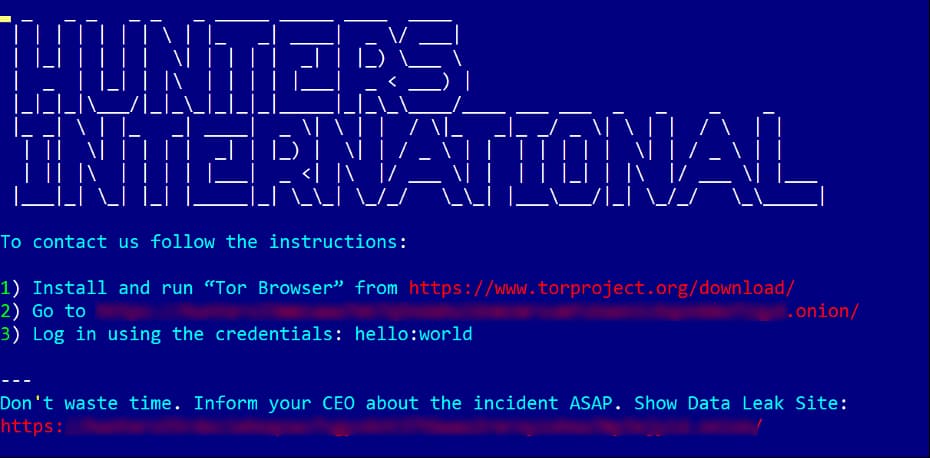
Hunters International refutes rumors that it is simply Hive under a different name. The group claims it is autonomous, saying it has bought the Hive infrastructure and fixed its source code. The group’s primary method of operation is data exfiltration rather than encryption; victims in the United States, the United Kingdom, Germany, and Namibia are among its primary targets.
Ransomware as a Service and Other Unusual Techniques
Hunters International uses a novel strategy, selling Ransomware-as-a-Service using Rust-language ransomware. Their approaches require generating two key sets in memory for file encryption, stored as the encrypted drive’s root with a .key suffix. GravityZone from Bitdefender has detected this file as a Trojan. When it comes to Ransom.Hunters, the team favors a less-is-more philosophy, opting for malware with fewer moving parts and fewer command-line options.

Revealing the Rise of Convergent Technologies
Will Thomas, aka @BushidoToken, a security researcher, uncovered shocking parallels and code overlaps between both parties, with a reported 60% similarity. This similarity hints at the consistency and continuity of Hive’s harmful actions.
The World-Wide Consequences: Aiming for Victims All Over
Despite ongoing debates on the connection between Hive and Hunters International, the broader picture highlights the ever-evolving nature of ransomware groups. The geographical reach expands as the group targets victims globally, posing a significant challenge for international cybersecurity efforts.

Read More:
- Strengthen Your Defense with a Robust Cybersecurity Checklist for the Shields Ready Campaign in 2023
- Learn About the Ethical Challenges Presented by Offensive Cybersecurity Operations and “Hacktivism”
- New Cybersecurity Regulations: A Step-by-Step Guide to Compliance
- The Power of Federated Learning to Change Data Privacy
- Navigating the Ethical Terrain of AI and Machine Learning step by step










