Last Updated on 22/11/2021 by Sunaina
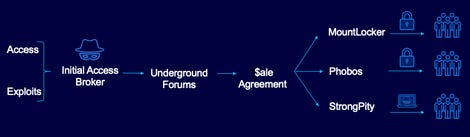
According to a recent BlackBerry study, an initial access broker known as “Zebra2104” has links to three harmful cybercriminal gangs, some of which are involved in ransomware and phishing. The BlackBerry Research & Intelligence team discovered that Zebra2104 served as a gateway for ransomware gangs such as MountLocker and Phobos, as well as the StrongPity APT. Access was granted to a number of compromised firms in Australia and Turkey.
The StrongPity APT targeted Turkish healthcare firms as well as smaller enterprises. According to BlackBerry, based on their study, the access broker “has a lot of personnel or they’ve put up some massive ‘hidden in plain sight’ traps throughout the internet.”
Moreover, According to the report, their investigation led them to think that the MountLocker ransomware gang was collaborating with StrongPity, a 2012 APT outfit that some said was a Turkish state-sponsored group.
While it may appear unrealistic for criminal organisations to share resources, the researchers discovered a link facilitated by a fourth; a threat actor named Zebra2104, which they believe to be an Initial Access Broker (IAB). There is, without a doubt, a full cornucopia of danger groups cooperating, much beyond those listed in the blog.
That one domain led them down a road where they discovered many ransomware assaults as well as an APT command-and-control server (C2). The route also disclosed an IAB’s infrastructure — Zebra2104. IABs often get access to a victim network before selling it to the highest bidder on underground forums on the dark web. Depending on the aims of their campaign, the successful bidder will later distribute ransomware and/or other financially driven malware into the victim’s organisation.
The BlackBerry Research & Intelligence team then analyzed WHOIS registration information and other data to uncover connections between the Phobos ransomware and MountLocker. According to the study, the domains resolved to IP addresses provided by the same Bulgarian ASN, Neterra LTD. While they were unsure whether the access broker was situated in Bulgaria, they concluded that the firm was just being exploited.
According to the researchers, the “interlinking web of malicious infrastructure” outlined throughout the paper demonstrated that cybercriminal gangs are operated like global corporations.










