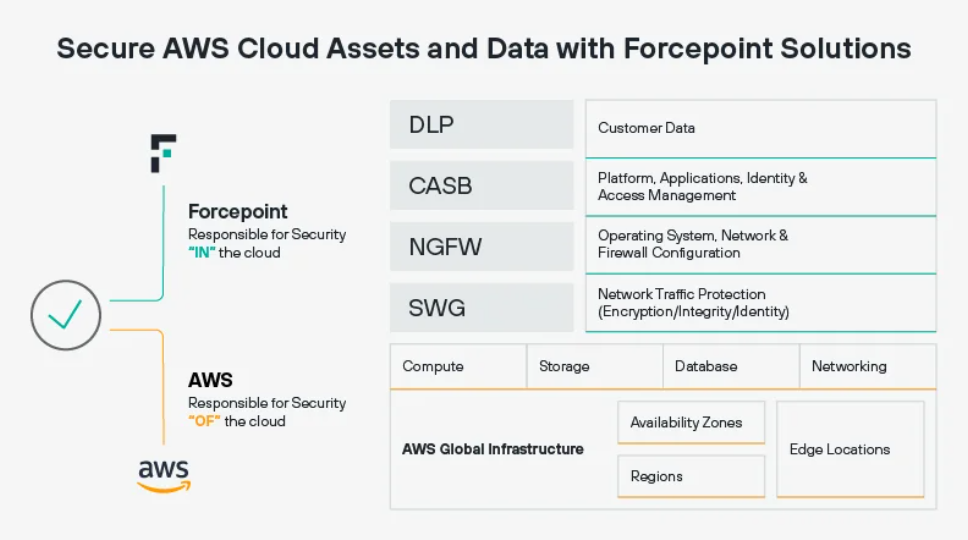
Using CASB to Manage Critical Assets and Establish User Access
According to Thomas Likas, global head of security architecture and engineering at Takeda Pharmaceuticals, using the cloud access security broker's three features - API-level...
‘Credential stuffing’ affects 1.1 million people in New York
Attorney General Letitia James of New York says her office has notified 17 companies about 'credential stuffing' cyber intrusions that have affected over 1.1...
Hundreds of real estate websites using cloud video hosting providers, victimized by online skimming...
Researchers have warned that hundreds of real estate websites are being targeted by online skimming attacks using a cloud-based video storage service.
Attackers are utilizing...
Operators have begun to rebrand, as ransomware assaults have decreased
Positive Technologies examined the threat landscape in Q3 2021 and discovered that attacks against individuals, as well as assaults utilizing remote access malware, had...
Cobalt Strike Beacon executed using MSBuild
Two independent malicious operations using MSBuild to launch the Cobalt Strike payload on targeted PCs were detected by a researcher from Morphus Labs.
The attackers...
Passwords saved in many browsers by RedLine Malware Pilfer
According to research published by AhnLab ASEC, users should avoid using the auto-login option included in many popular web browsers.
On cybercrime forums, the RedLine...
Predictions for Cyber Regulation in 2022, let’s know
According to Andy Watkin-Child, founding partner of the Augusta Group, a cybersecurity and risk consultancy business, the US government has taken considerable steps to...
Using Electromagnetic Emanations to Spot Evasive Malware on IoT Devices
Researchers have developed a unique strategy that uses electromagnetic field emanations from the Internet of Things (IoT) devices as a side-channel to gain accurate...
Two Israeli news organizations hacked, a threatening message and a photograph shared
Early Monday, two prominent Israeli news sites were hacked with a menacing message that looked to be tied to the murder of a top...
China harvested vast amount of data from Western social media, says report
According to a new revelation from The Washington Post, China is mining Western social media to provide information about outside targets to its army...